Power Platform Compliance Week Day 1 – Top 10 Compliance Risks in Power Platform (and Why They’re Overlooked)
-
Admin Content
-
Oct 27, 2025
-
234
Power Platform Compliance Week Day 1 – Top 10 Compliance Risks in Power Platform (and Why They’re Overlooked)
Microsoft Power Platform—comprised of Power BI, Power Apps, Power Automate, and Power Virtual Agents—is a powerhouse for business transformation. Its low-code design empowers "citizen developers" and IT teams alike to create apps, automate workflows, analyze data, and build chatbots with minimal effort. But with great power comes great compliance responsibility. As organizations rapidly adopt Power Platform to digitize operations, compliance risks can silently creep in—and often go unnoticed.
On Day 1 of Power Platform Compliance Week, we’re kicking things off with a deep dive into the top 10 compliance risks most often overlooked —and why they remain under the radar.
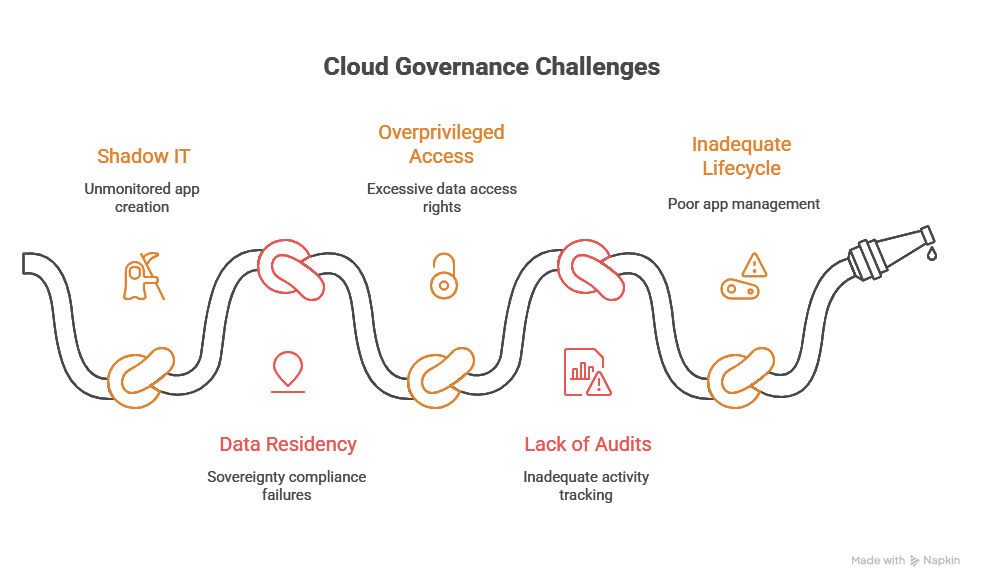
1. Shadow IT and Unmonitored App Creation
One of the key benefits of Power Platform is its democratization of app development. However, this also introduces a significant risk: Shadow IT . Employees may create apps, workflows, or dashboards without IT's knowledge, bypassing governance controls altogether.
These unsanctioned apps may access sensitive data or integrate with third-party services, leading to data leakage, noncompliance with industry regulations, and exposure to security vulnerabilities. Since Power Platform is so easy to use, organizations may fail to implement proper governance early on, allowing non-compliant solutions to flourish under the radar.
2. Data Residency and Sovereignty Concerns
Power Platform stores data in Microsoft’s cloud, but unless explicitly configured, users may not know where that data is hosted. This can pose major issues for organizations subject to data residency or sovereignty laws such as GDPR, HIPAA, or national data localization mandates.
Many overlook this risk because Power Platform offers pre-built connectors and quick integrations, which abstract away the underlying infrastructure. Without a clear data residency strategy, apps and flows might store or process data in non-compliant jurisdictions.
3. Overprivileged Access Controls
Default access permissions in Power Platform can be deceptively permissive. A user creating a Power App may grant broader access than necessary to data sources like SharePoint, SQL, or Dataverse. These overprivileged roles can lead to unauthorized data access or even accidental data exposure.
Why is this overlooked? Because permissions are often configured by users without deep security or compliance training. The simplicity of role assignment hides the complexity of access control implications.
4. Lack of Audit Trails and Monitoring
Many organizations fail to activate or monitor audit logs for Power Platform usage. Without comprehensive logging , it's nearly impossible to track who did what, when, and where—making it difficult to investigate incidents or prove compliance during audits.
Audit capabilities exist, but they must be enabled intentionally, often requiring integration with Microsoft Purview or Defender. Since these tools are optional add-ons and not always configured by default, audit coverage may be insufficient or nonexistent.
5. Inadequate Lifecycle Management of Apps and Flows
Applications and automated workflows often start as proof-of-concept or temporary tools, but they may remain in use indefinitely. Without a defined lifecycle management strategy, old or deprecated apps can accumulate risks—such as outdated connectors, abandoned ownership, or unresolved security vulnerabilities.
This risk goes unnoticed because there's no built-in process to deprecate, archive, or review unused solutions. Apps live in personal environments or across departments, lacking centralized oversight.
6. Third-Party Connectors and Unverified Integrations
Power Platform offers hundreds of connectors to external services, and users often plug in third-party APIs without understanding the security or compliance implications. Many of these custom connectors are not vetted for compliance, exposing organizations to potential data breaches or regulatory violations.
Why is this overlooked? Because the interface for adding connectors is so streamlined that users may not question its compliance impact. The danger lies in the fact that connectors can bypass internal controls and transmit data outside the organization's boundaries.
7. Poor Data Classification and Sensitivity Labeling
Most organizations use Power Platform to process business-critical or even sensitive data. But without data classification and sensitivity labels , these apps treat all data the same—whether it’s public, confidential, or restricted.
The problem is often due to misalignment between Power Platform and the broader Microsoft Information Protection strategy. Unless explicitly configured, sensitivity labels don’t propagate across apps or flows, leaving sensitive data unprotected or misused.
8. Noncompliant Use of AI and Automation
As AI features like Copilot are increasingly embedded in Power Platform, organizations risk noncompliant AI usage —particularly when models generate or process sensitive or regulated data. Automated decisions made through Power Automate can also cross into regulated domains like HR, finance, or healthcare.
These risks fly under the radar because automation and AI capabilities are marketed as productivity boosters. Without governance policies tailored to AI, organizations might unknowingly violate fairness, accountability, or transparency requirements.
9. Personal Environments and Data Silos
Each licensed user in Power Platform can create a personal environment , which is essentially a private sandbox for building apps and flows. While useful for experimentation, these environments often become data silos—cut off from IT oversight and governance policies.
The danger? Sensitive data can be processed or stored without encryption, monitoring, or lifecycle controls. These personal environments are easy to overlook because they’re individualized and not part of standard environment governance reviews.
10. Misconfigured DLP (Data Loss Prevention) Policies
Microsoft offers Data Loss Prevention (DLP) policies for Power Platform, allowing organizations to restrict which connectors can be used together. However, many companies either don’t configure these policies or apply them inconsistently across environments.
As a result, users might unknowingly send data from a secure source to an unsanctioned external system. This risk is overlooked because it requires proactive configuration and continual policy updates—tasks often sidelined by IT due to time or resource constraints.
Closing Thoughts: Proactivity is the Best Protection
The Power Platform offers unprecedented agility, but that same speed and ease can lull organizations into a false sense of security. The risks we’ve outlined today aren’t theoretical—they’re happening now, across industries, and often without detection. Overlooking these risks can lead to serious regulatory breaches, reputational damage, and loss of customer trust.
Addressing these hidden compliance pitfalls starts with awareness and governance. Organizations must align their Power Platform strategy with compliance teams, set up robust monitoring, and instill a culture of secure and compliant development from the ground up.
As we continue through Power Platform Compliance Week, we’ll explore how to build a governance framework that scales with your business—without stifling innovation.